Exposure remediation through the attacker’s lens
WithSecure™ Elements Exposure Management

Discover and act on your digital exposures before cyber criminals do
WithSecure™ Elements Exposure Management (XM) is a continuous and proactive solution that predicts and prevents breaches against your company’s assets and business operations. Elements XM provides visibility into your attack surface and enables the efficient remediation of its highest-impact exposures through a unified view, thanks to our exposure scoring and AI-enabled recommendations. Get one solution for 360° digital exposure management and visibility across your external attack surface and internal security posture, to proactively prevent cyber-attacks.
Product overview
The shifting cyber security environment
The shift from reactive to proactive cybersecurity has long been a priority for security professionals, but satisfactory solutions have been in short supply. In today’s digital age, businesses face an ever-evolving threat landscape, with new vulnerabilities emerging constantly and the development of AI enabling new types of cyber-attacks. Organizations have increasingly hybrid environments with unclear borders. The challenge is not only to protect systems and data, but also safeguard business continuity against digital supply chain threats and potential compromises. Additionally, many organizations need to bridge the gaps to meet the NIS 2 Directive*.
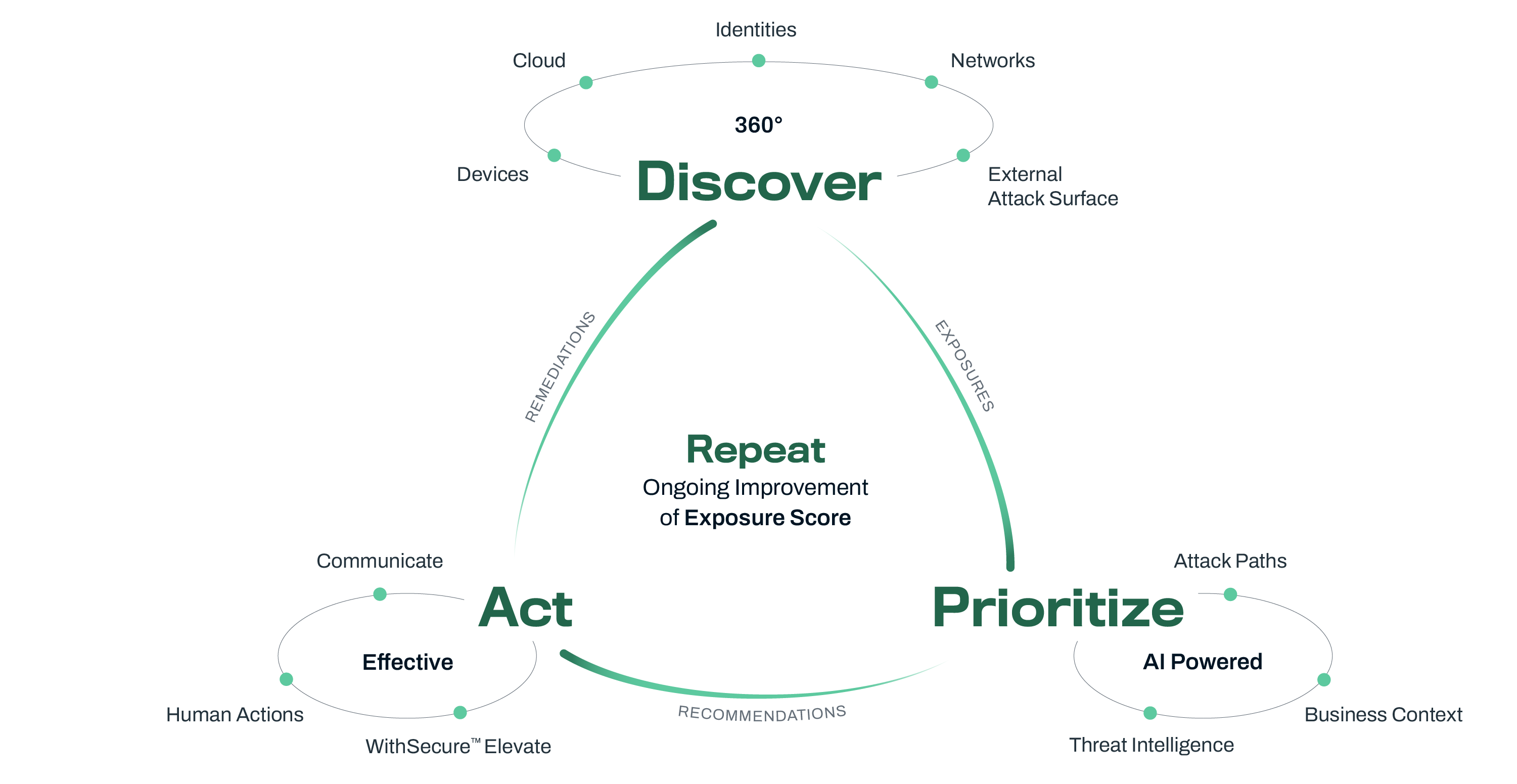
Identify potential attack paths to your critical assets with 360° visibility
The innovative and AI-powered WithSecure™ Elements Exposure Management (XM) addresses these challenges by providing comprehensive exposure management tools. WithSecure is the thought-leading Exposure Management provider for European SMEs and MSPs, and for organizations that want cyber security done the European Way. Our Elements Exposure Management provides capabilities and processes that evaluate how accessible and exposed an organization’s digital assets are, and how easy it is to exploit them. The solution offers continuous recommendations by simulating attack paths, identifying critical vulnerabilities, and offering risk focused outputs to proactively strengthen defenses. Moreover, Elements XM helps you be more compliant with regulations, like the NIS 2 directive*.
NOTE: * NIS 2 art. 21.2(e) mandates companies to have security in network and information systems acquisition, development and maintenance, including vulnerability handling and disclosure.
Maximize your cyber resilience with minimum effort
Elements XM combines data from your external attack surface, identity management systems (e.g. Entra ID), devices, network, and cloud services (Azure, AWS). The solution enriches this data with real-time threat intelligence and business context for a holistic security approach. The AI-powered recommendations include guidance for technical teams on how to take the most impactful actions quickly and make security risks easy to understand for business decision-makers. Our additional WithSecure™ Elevate service allows a specific finding, recommendation or attack path to be sent to us for further analysis. This consultation from our experts ensures the validity and priority of the elevated item.
WithSecure™ Elements Exposure Management uses patent-pending AI-based attack path simulation technologies for heuristic exposure hunting and adversarial exposure validation.
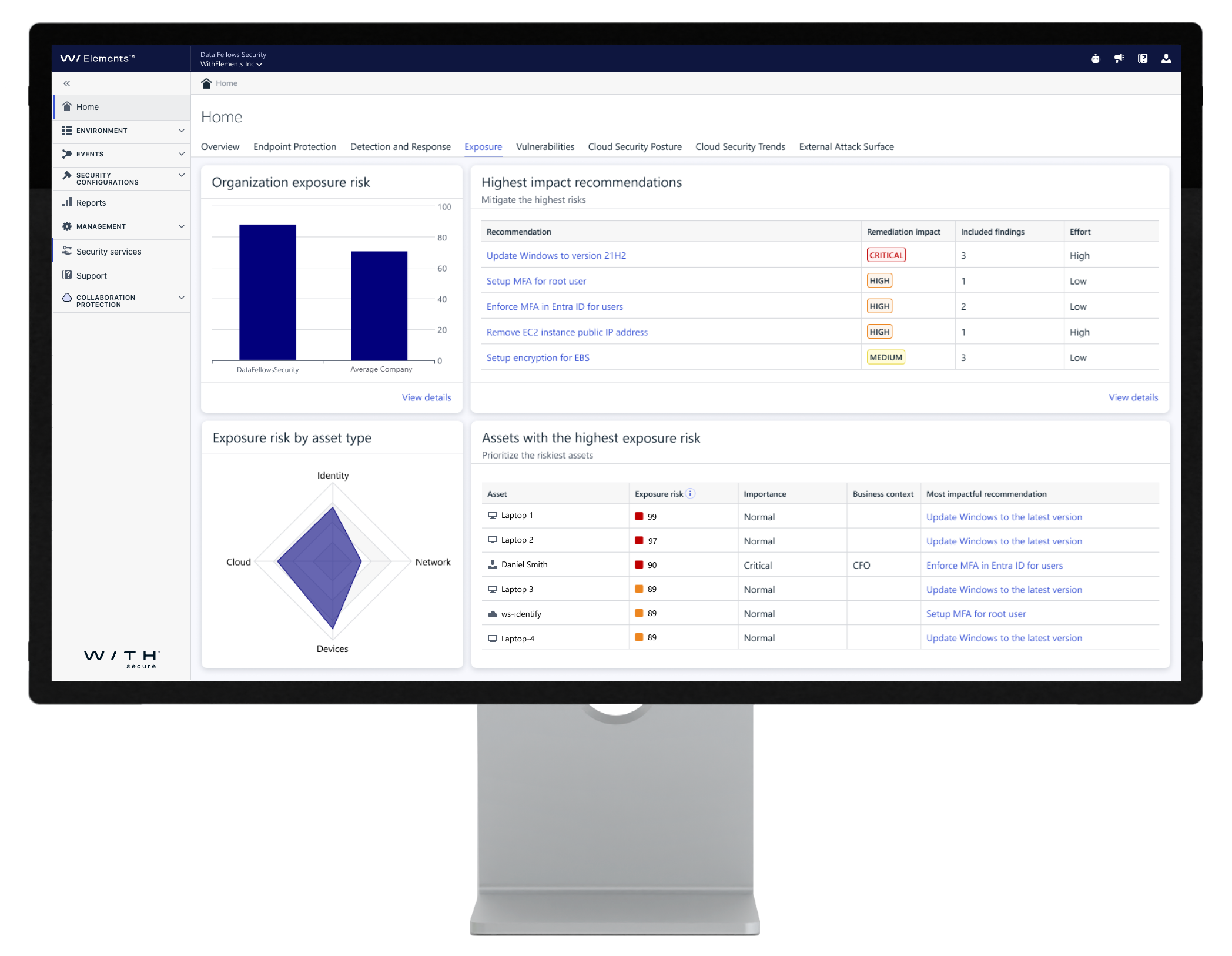
Understand your business risk and recommended actions via Exposure Dashboard.
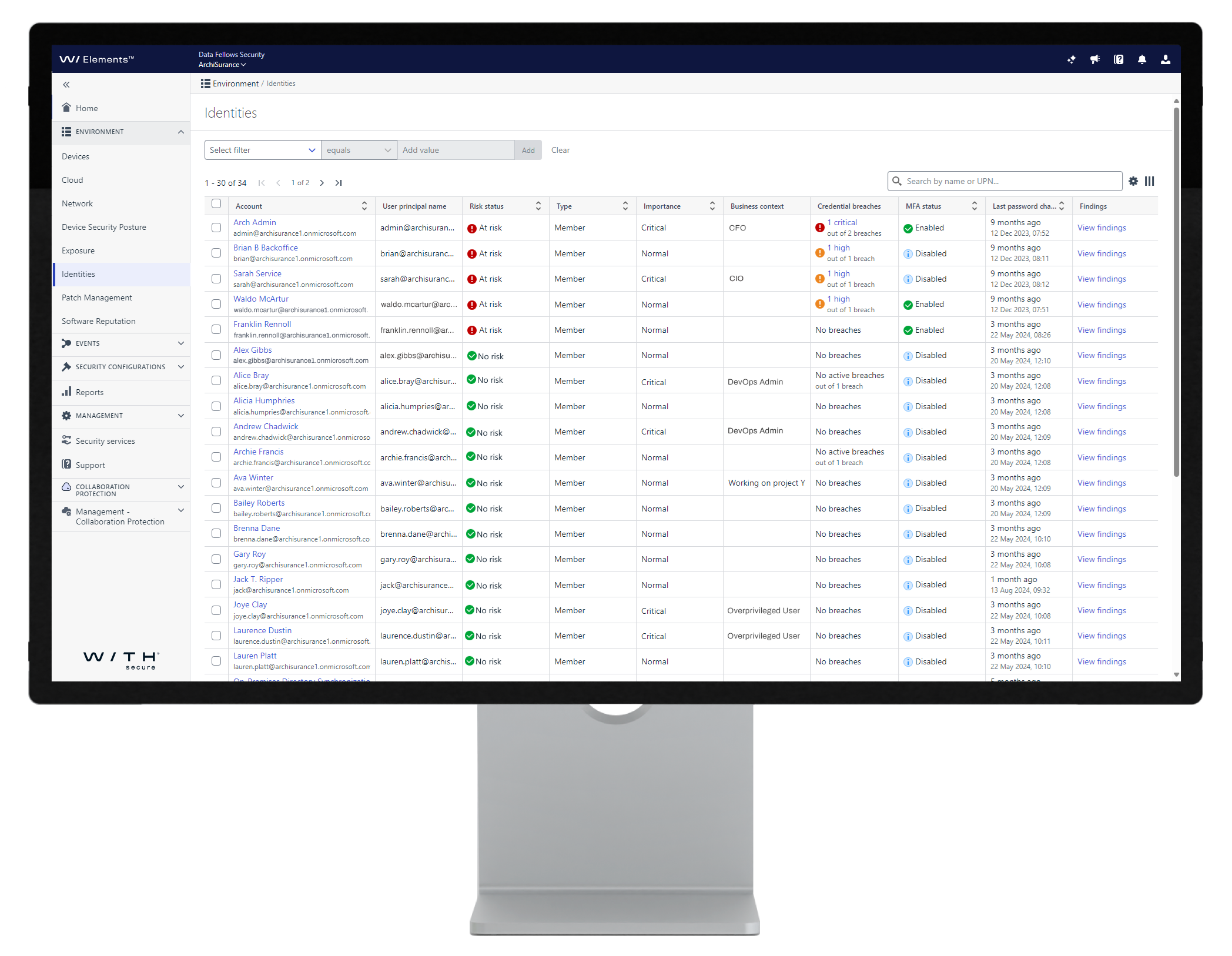
Use data on digital identities to tackle identity-based risks.
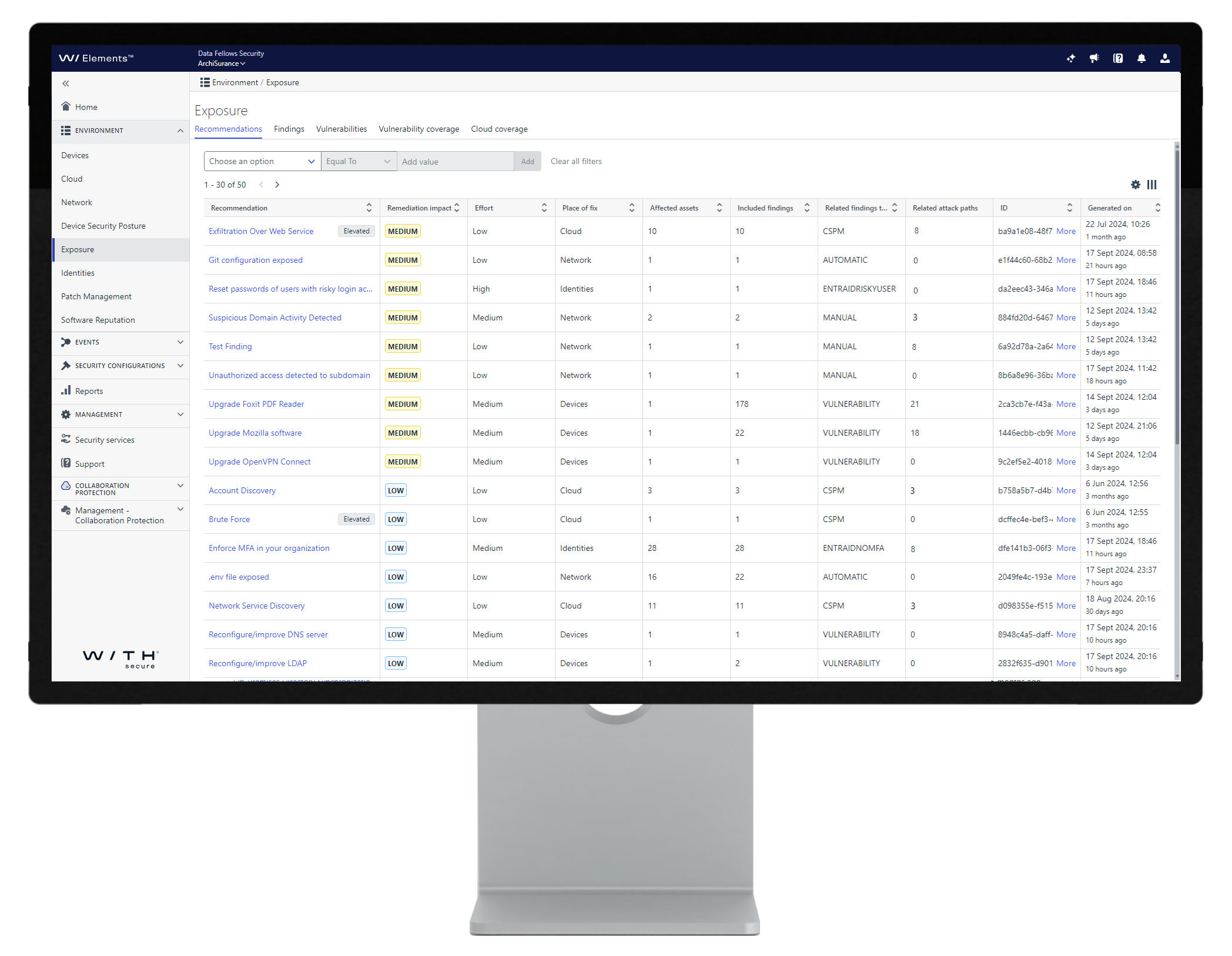
Use your time effectively by starting remediation from exposures with the highest impact and lowest effort, using our AI-powered recommendations.
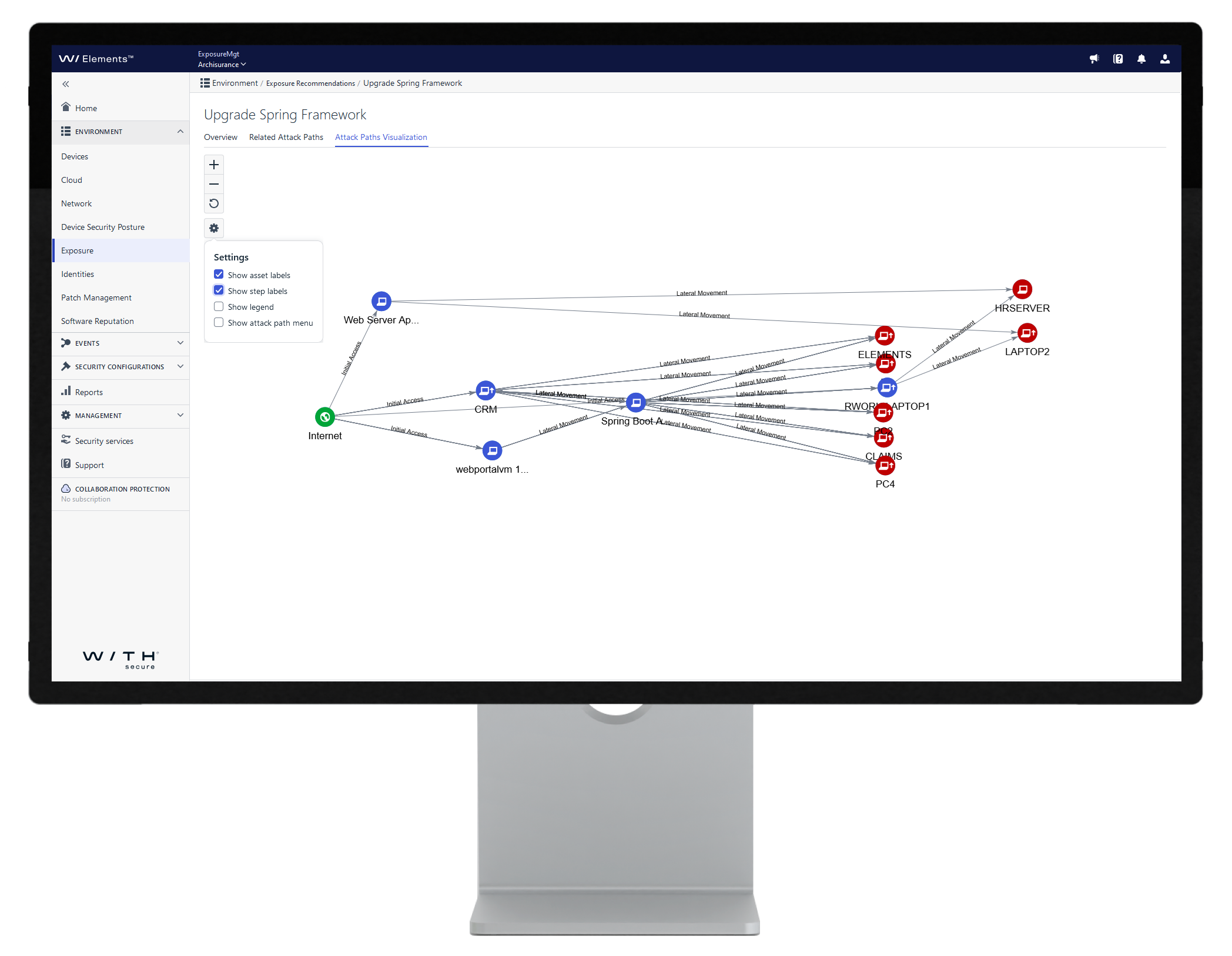
See the visualized the attack paths related to a recommendation, enabling you to dive deeper into the underlying reasoning.
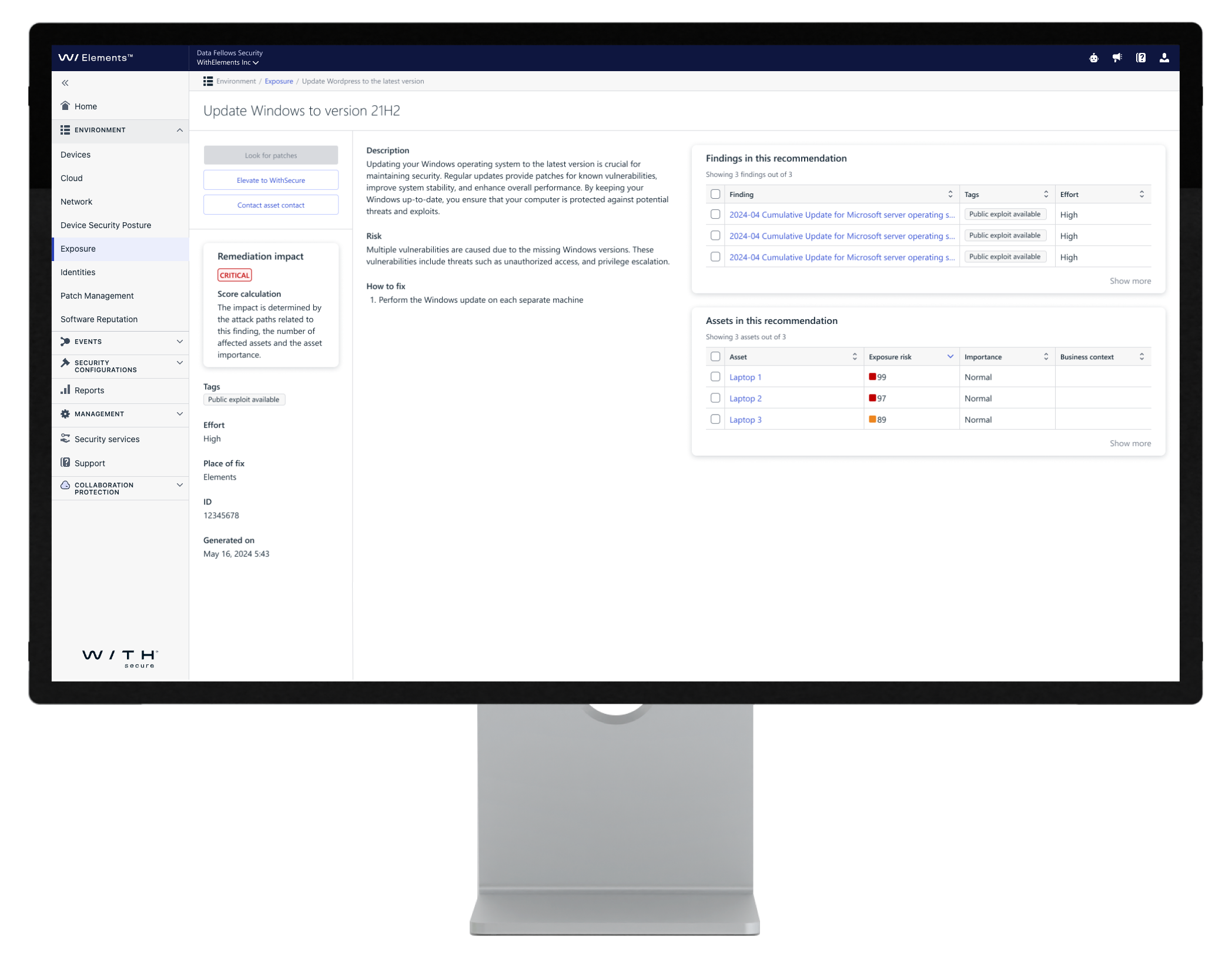
Get actionable remediation guidance and communicate about the remediation process for smooth collaboration.
- Option1
- Option4
- Option3
- Option5
- Option2

WithSecure Elements XM now available on AWS Marketplace.
If you are an AWS customer, you have an additional channel to purchase WithSecure Elements XM directly from the AWS Marketplace or through a partner with AWS Marketplace access.
Stay ahead of potential threats with the WithSecure Elements Exposure Management (XM) solution!
XM Interactive Demo
Curious to see Exposure Management in action? Our interactive demo lets you explore XM’s capabilities firsthand—no sign-up required.
Take a deep dive into WithSecure™ Elements Exposure Management
Supported systems
Secure environments that make up your attack surface
Our multi-environment approach covers the following assets and environments:
- External Attack Surface (EASM)
- Cloud services including Azure and AWS platforms
- Identities including as Entra ID
- Managed devices including workstations and servers
- Network including network equipment
Ready to maximize your cyber resilience with minimum effort?
Unlock the power of WithSecure™ Elements Exposure Management to discover, prioritize, and act on critical exposures. Take the next step in securing your organization’s digital landscape by completing the form and our sales representative will reach out to you as soon as possible.
Related content
Strengthening Cybersecurity Defenses: Understanding Exposure Management
Master the art of exposure management to preemptively identify and mitigate cyber threats. Our guide provides essential strategies for dynamic risk control and proactive cybersecurity.
Read moreThe power of prevention: the role of exposure management in 2024
Every IT security professional we speak to would choose to prevent a breach, rather than stop it once located. That’s why exposure management is the next big thing in cyber security. Only by gaining a view of your entire attack surface can you hope to prevent breaches occurring.
Read more