Stay Ahead of Evolving Threats with XDR: Download Your Free Guide Today
Cyber threats are more sophisticated than ever—malware is just the beginning. To truly protect your hybrid IT environment, you need a security solution that goes beyond endpoints, securing identities, email, collaboration tools, and more. Extended Detection and Response (XDR) delivers the advanced protection you need to detect and stop attacks before they spread.
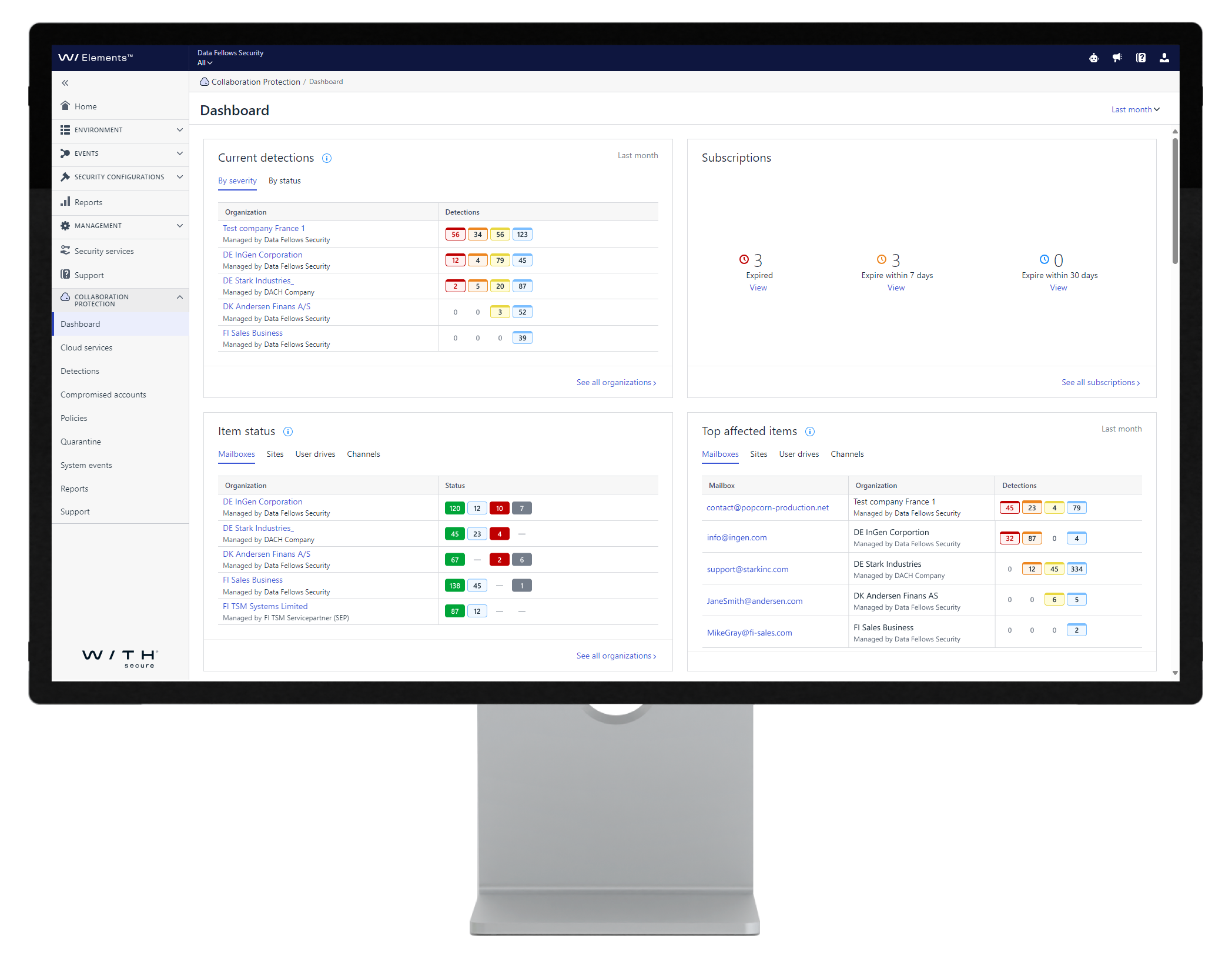
Discover the Power of Extended Detection and Response (XDR)
Our comprehensive eBook, "Why Do I Need XDR?", explains how XDR provides the advanced visibility and protection your organization needs.
Inside, you’ll explore:
The evolution of cyber threats and why traditional defenses are no longer enough.
Key advantages of XDR, including end-to-end threat detection across your entire IT estate.
Actionable insights to fortify your security strategy against advanced attacks.
Interesting facts:
90% of organizations reported at least one identity-related incident in the last 12 months*
71% spike in cyberattacks caused by exploiting identity*
26% of ransomware attacks happens within Europe*
*IBM’s Cost of a Data Breach Report 2023 by Ponemon (24 July 2023)
Let WithSecure CPO, Pilvi Tunturi & Product Director, Mika Arasola explain why your organization needs XDR!
Also, don't miss out on our essential guide which provides invaluable insights into the next generation of EDR solution.
What are the key features of an effective XDR solution?
















Take Control of Your Cybersecurity Today
Don’t let gaps in your defenses leave you vulnerable. Discover how XDR can transform your security strategy and protect your organization from advanced threats.
👉 Download the Free eBook Now.
Gain the insights you need to stay ahead of attackers. Fill out the form to get your copy instantly!