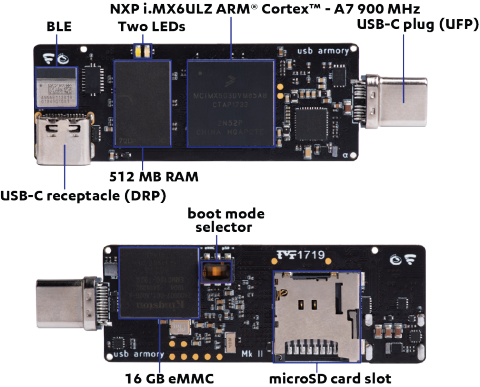
USB armory
The USB armory is an open source hardware design, implementing a flash drive sized computer.

The USB armory is the world's smallest secure computer.
It can safeguard data and run trusted applications, preventing unauthorized access or execution. Minimal attack surface, vast performance and capabilities. Fits right in your pocket, your laptop, your servers.
Compact. Customizable. Secure.
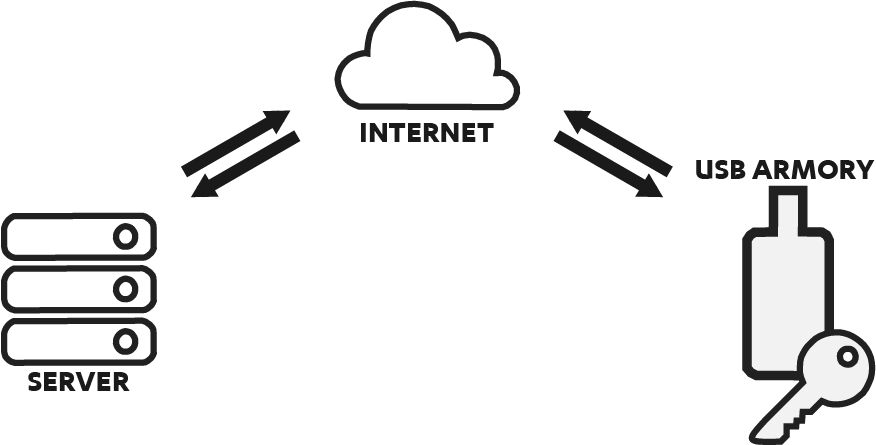
The capability of implementing arbitrary USB devices in combination with the USB armory speed, the security features and the flexible and customizable operating environments, makes the USB armory the ideal platform for all kinds of personal security applications.
-
pdf
- 1 MB
What are the applications?
The USB is a prime platform for the following applications:
Security features
The USB armory incorporates a vast number of features that can support a wide variety of security architectures. Its capabilities allow the safe storage of data as well as the trusted execution of operating environments and their applications, natively on the device itself.
Beyond simple smartcards or security tokens, the USB armory is a personal, self-contained, secure server.
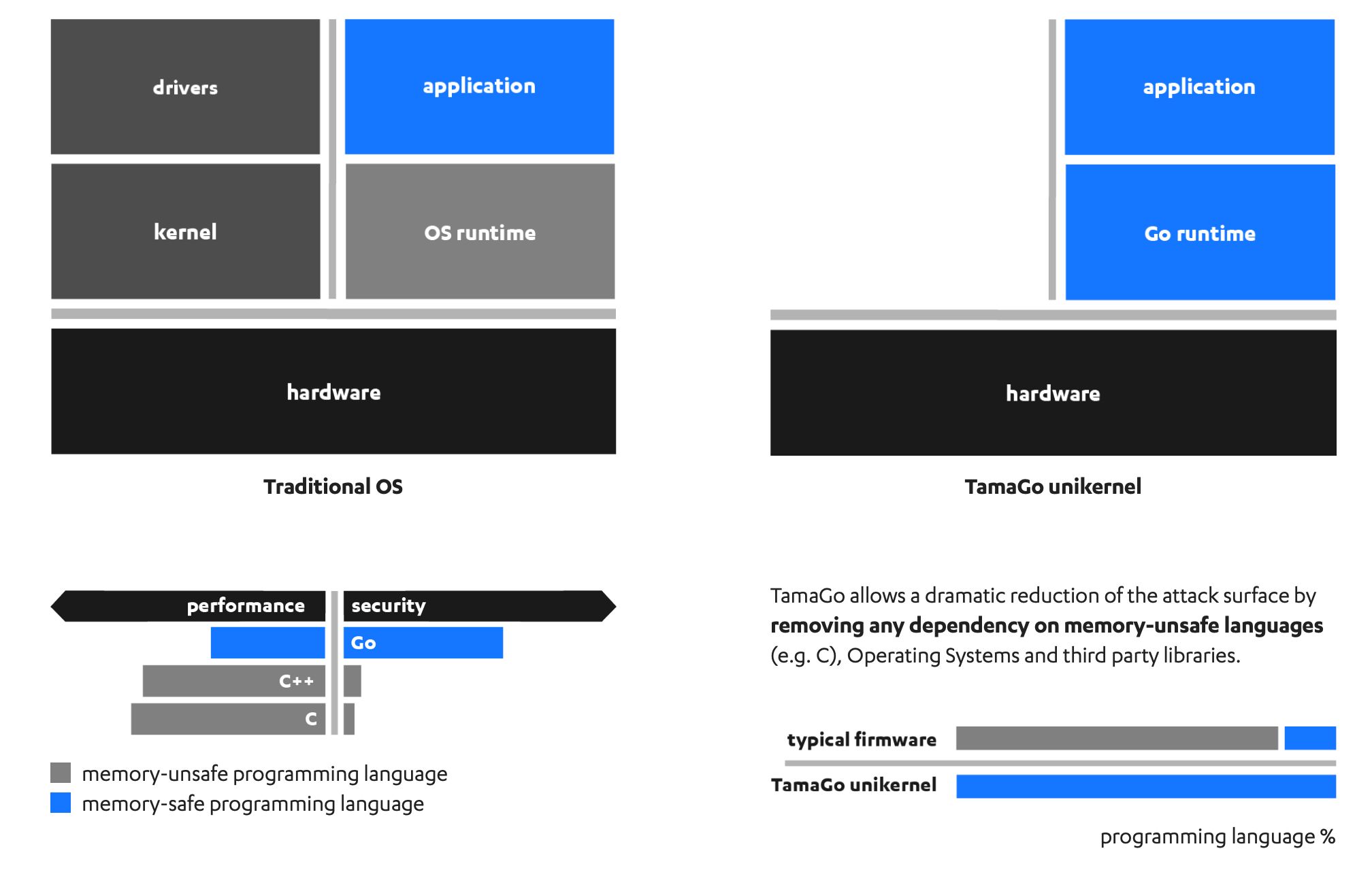
TamaGo
In addition to native support for standard operating environments, such as Linux distributions, the USB armory is directly supported by TamaGo, an WithSecure Foundry developed framework that provides execution of unencumbered Go applications on bare metal ARM® System-on-Chip (SoC) processors.
Example use cases

Amory Drive
The USB armory provides secure execution of cryptographic operations and data storage.
The user can unlock the USB armory over Bluetooth, authorizing only need-to-know contents, to ensure safe operation even on untrusted laptops.
How to order
The USB armory is assembled entirely in Italy and is available for ordering from selected stores as listed below. Additionally custom/bulk order inquiries can be placed directly by contacting usbarmory@withsecure.com
Product configuration
Standard orders
| Model | Configuration |
| UA-MKII-ULZ-512M | USB armory Mk II • i.MX6ULZ 900 MHz • 512 MB RAM • enclosure |
| UA-MKII-DA | Debug accessory for the USB armory Mk II |
Custom / bulk orders
| Model | Configuration |
| UA-MKII-UL-512M | USB armory Mk II • i.MX6UL 528 MHz • 512 MB RAM |
| UA-MKII-UL-1G | USB armory Mk II • i.MX6UL 528 MHz • 1 GB RAM |
| UA-MKII-ULZ-1G | USB armory Mk II • i.MX6ULZ 900 MHz • 1 GB RAM |
| UA-MKII-ENC | Enclosure for the USB armory Mk II |
Related resources
Want to customize / bulk order or talk in more detail?
Complete the form, and we'll be in touch as soon as possible.