Navigating NIST CSF 2: A Comprehensive Guide for Business Leaders and CISOs

The NIST Cyber Security Framework has helped secure organizations for nearly nine years.
It’s proven to be an invaluable tool in that time, so the new draft of CSF 2.0 is good news – right?
The answer is a qualified ‘yes’.
Why? The Framework is updated for a new decade, and also now reflects the increasing role of cyber risk in the operations of many organizations. It’s a qualified ‘yes’ because one of the biggest changes is governance and oversight – and that comes with risks and rewards in equal measure.
Let’s dive in and find out more about those updates.
Core changes to the NIST Cyber Security Framework
In addition to the original functions in the 1.1 version, the new framework adds a ‘Govern’ function. This highlights the importance of senior leadership accountability – and that means building a risk-aware culture, and measurable outcomes to assess the effectiveness of any cyber security program.
Therein lies the potential trip hazard: apply or enforce these wrong, and you risk ending up with a Board or senior management that applies unreasonable measurements, or asks too little or too much.
There are five more significant changes worth knowing about:
- More focus on Supply Chain Risk Management – and continuous improvement. This includes guidance for senior leaders. Bearing in mind the resurgence in Supply Chain cyber attacks, this is a good thing. A core part of this is the use of
- Secure Software Development Practices, making it part of everyday software development and service lifecycles. It’ll be interesting to understand how this links with growing mainstream use of SaaS for all of the things. It’s also a painful overhead if you’re writing stuff in-house.
- Increased emphasis on the integration of Threat intelligence with your organization’s SIEM.
- Data Security – reflecting the importance of ongoing monitoring in identifying and responding to data breaches. Ensuring data is collected and secured before attacks and breaches is often of critical importance to timely and effective response.
- Preserve incident data, more emphasis on estimating and validating incident impact and tracking incident status. This might be linked to chain of custody and evidence preservation, two things dear to our incident responders’ hearts. Yet it’s unlikely that most incidents will end up in the law courts, so it’s likely this is connected to cyber insurance – and it also places an onus on incident responders – both in-house and external – to preserve data correctly.
- Recovery planning, coordination, communications, and availability of cybersecurity services is the final area. There’s more emphasis is placed on verifying backup integrity before restoration and ensuring asset integrity after recovery.
Four reasons why your Board (and you) will want to move to CSF2
You’ll get a more tailored, comprehensive approach to cyber security by upgrading to CSF 2.0. Here’s four reasons:
- Improve Stakeholder Confidence: CSF 2 will help your organization demonstrate a proactive approach to cybersecurity, reassuring customers, investors, and partners that it takes cybersecurity seriously
- Cost-Effective Investment: set priorities and allocate resources based on you organization's specific risk profile. The end result? Slash unnecessary expenses and maximize the impact of your investments
- Cybersecurity Resilience: create a robust incident response plan and recovery procedures, minimizing the impact of cyber incidents and cutting downtime
- Comprehensive Risk Management: By adopting the CSF, organizations get greater visibility into their risk landscape. Make more informed decisions to allocate resources and investments effectively.
Five things you (and your Board) want to watch out for if moving to NIST SCF 2
Make no mistake: this transition is a huge effort with equally brilliant payouts, but it’s not without risk. Top of our list are three things: the need for proper planning, effective communication and a comprehensive change management plan.
By addressing these risks proactively, organizations can minimize potential disruptions and ensure a successful transition to the updated framework.
Let’s get into a bit more detail:
- Lack of Understanding
Invest time and resources in educating their teams about the updated framework. Fail to understand the changes this framework will bring, and things could get tricky. - Implementation Challenge
Develop a detailed implementation plan that outlines key milestones, assigns responsibilities, and supplies a timeline for the transition. - Resource Constraints
You’ll need time, budget, and expertise. Organizations should conduct a thorough resource assessment to ensure they have what they need to make the transition successfully. - Non-Adoption
There is a risk of resistance from employees or teams resistant to change. To address this, foster a culture of cybersecurity awareness and engagement. Promote the benefits of the updated framework, provide clear guidance and support, and involve employees in the transition process – all of these can help overcome resistance and encourage adoption. - Who’s in charge?
We talked about accountability before – and this can be a double-edged sword. Do it right, and you know what the board wants to see, and the board knows what to ask for. Ask if you board is imposing it, or if the CISO organization is adopting it. Preferably both approaches result in an outcome-based cyber security approach – with complete communication all the way.
Your Board comms toolkit: NIST CSF for cyber risk management
The US National Institute for Standards and Technology (NIST) Cyber Security Framework 2.0 builds on previous efforts that set out guidelines, best practices and standards organizations can use to manage cyber security risk. This makes the CSF a useful tool for security managers, CISOs, IT Directors, CISOs and the boards that oversee them to make sense of what can be a complex, fluid environment.
The Cyber Security Framework is built around five principles (Identify, Protect, Detect, Respond and Recover) which are then used to build a current profile that can then be matched against the desired target state. There’s also a set of steps – Implementation Tiers – to guide organizations through the process of moving to a higher level of ability and maturity. It’s actually easier to show it in a diagram, so we’ve put a couple in here:

Caption1: A simple framework can give a quick understanding of maturity – but context is vital
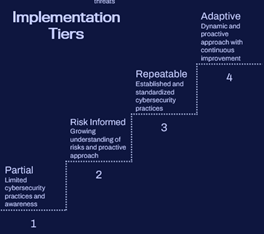
Caption 2: Implementation tiers are also helpful in communicating maturity and progress. But those looking for accountability need to set realistic goals.
Look at this from both points of view: the security team knows how to go about measuring and communicating the current state of cyber security for their organization – and moving to the senior manager and Board side of things, there’s a clear process by which they can understand the current state, process and what needs to happen to get to a good place. It’s also a great way to test the impact of different types of investment and priority.
Conclusion
NIST CSF2 has huge potential for organizations looking to both understand and upgrade their cyber security. It’s got tools that ensure accountability – and just as importantly provide clear canvases for making the case for investment and prioritization of efforts. Our Incident Readiness and Response team has already done the hard work to help organizations familiarize themselves with the new Framework, perform gap analyses and readiness assessments, customize the framework to your organization’s needs and to actually implement and execute the resulting plan.
To hear from three world-class CISOs on what CSF2 means for their organizations, watch on-demand our NIST CSF2 webinar.
Want to find out more?
Complete the form to chat with us about how we can help you with your cybersecuity needs.