Dynamic risk scoring: combining security with freedom
Tap into dynamic threat intelligence trends through our enhancements for Elements Vulnerability Management
A conversation between a customer and their Managed Service Provider
Customer:
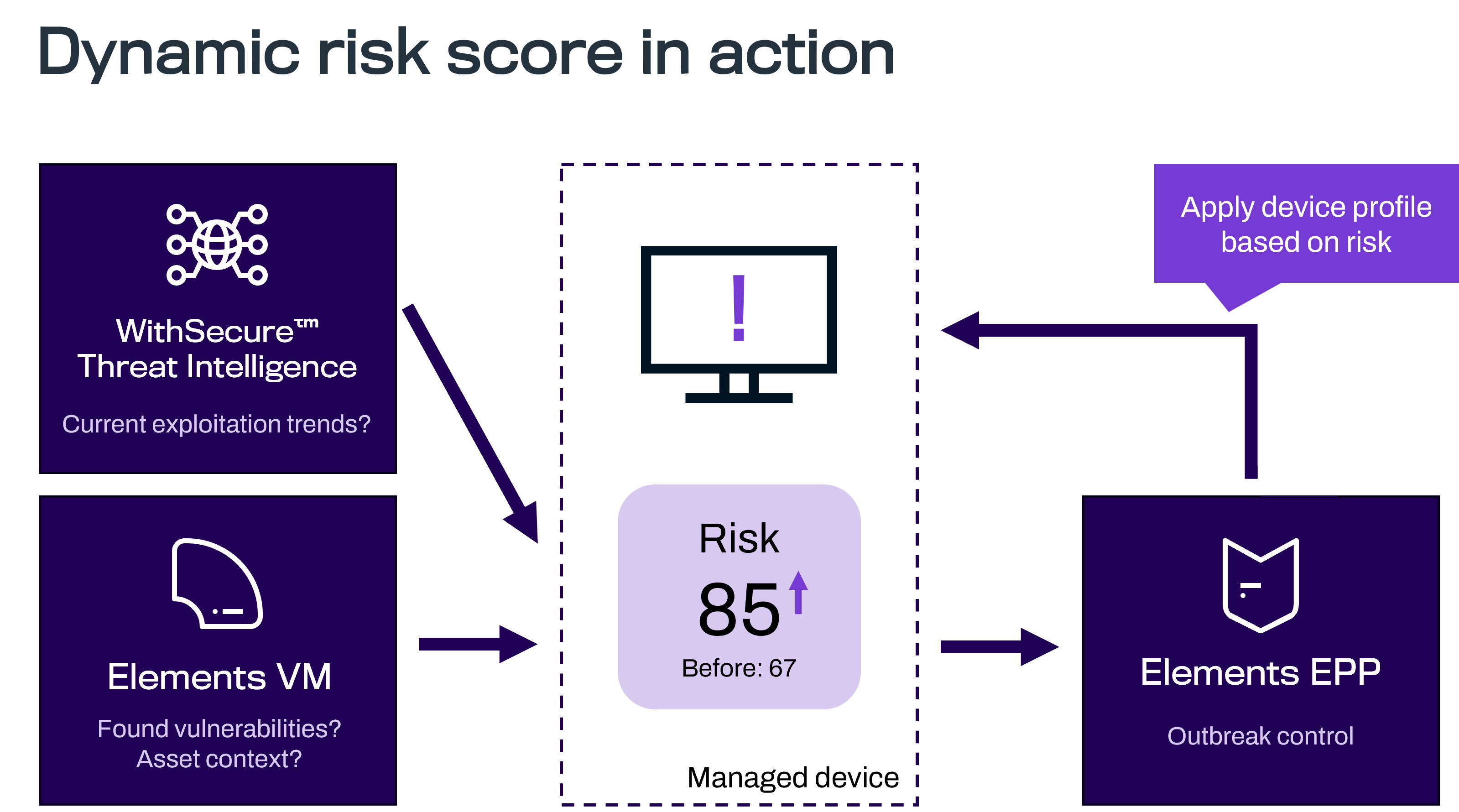
Yesterday, when I closed my computer, Elements reported that one of my assets had a total risk score of “67/Moderate”. Today, that same score is showing as “85/Severe.” There has been no re-scanning or other activities overnight. Why has the score changed?
MSP:
WithSecure's Threat Intelligence has discovered that a proof-of-concept exploit for one of the vulnerabilities has been published on the Internet, and Elements Vulnerability Management automatically boosted the score to show that the risk level is higher. Furthermore, if WithSecure finds that a real exploit already exists for this vulnerability, it will automatically boost the score again. By doing this, it becomes a higher priority in your organization's list of devices at risk, and should be addressed even quicker than normal.
This is done because the risk level changes depending on certain factors, even though the affected software hasn't changed at all. This way, it can be brought to your attention, and ours, much quicker. Actually, the score can also go down if it is determined that the risk is lower than originally thought.
But that's not all! As you also use Elements Endpoint Protection, we have configured a special WithSecure Outbreak Control rule in your security configuration. If the risk score is boosted over a certain level, we will prevent incoming connections from the Internet, protecting your vulnerable device from this remote exploit. And the best thing is, once that service is patched and no longer vulnerable, Elements will automatically allow those connections again.
Customer:
So, nothing to worry about?
MSP:
Well, we still need to fix the problems as soon as the vendor releases patches for them, but you don’t need to panic, WithSecure has got your back at all times!
But what does this actually mean?
Every device or asset can pose a risk to your organization, and Elements Vulnerability Management (EVM) is designed to help you manage those.
The Asset Risk value helps you identify which of your assets pose the highest risk in your company environment. This value can be used to prioritize the remediation of detected vulnerabilities, based on their potential impact.
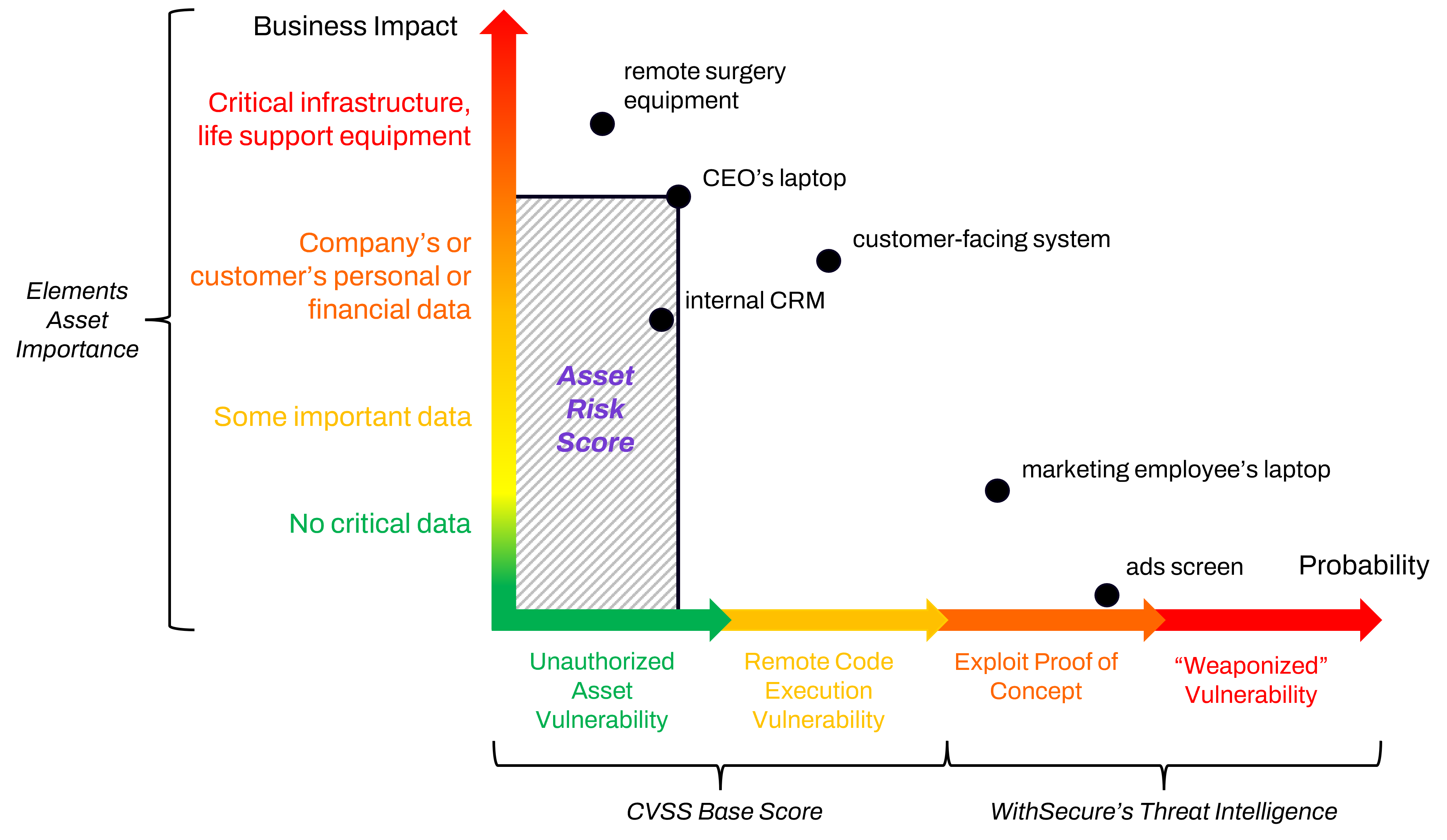
In this example, we consider that some assets, for example the CEO’s laptop, and surgery equipment, are more business critical than an advertising screen. The criticality of these devices is easily configured in Elements Vulnerability Management (EVM). Consequently, any vulnerabilities on these business-critical devices naturally cause higher risks.
However, the probability of having exploitable vulnerabilities affecting an asset can also change over time.
For instance, a vulnerable asset may be more at risk if there are active exploits against its vulnerabilities. By using Threat Intelligence data gathered by WithSecure, we can present the current threat level with the most up to date information.
When these threat intelligence data feeds indicate a change related to the detected vulnerabilities, this information is then presented to the EVM admin in the form of a modified Risk Score. When the Threat Intelligence data shows that exploits have become less prevalent, the score is automatically lowered in response.
By using this increased risk level from EVM, the administrator can very quickly prioritize the patching of the asset or take some other remedial action if the software vendor has not yet released a patch for it.
Moreover, because of the way WithSecure Elements can combine Vulnerability Management and Endpoint Protection (EPP) into a tightly integrated ecosystem, your Elements EPP can automatically increase the security of your assets. It does this via the Outbreak Control functionality, which can react to the increased risk score and select an even stricter security profile than the one normally used.
Consider, as an example, a content management system (CMS) that is accessed by your Sales team (using SSO) when out in the field to access data not on your public website.
If the CMS software is found to be vulnerable, and remotely exploitable, Outbreak Control could select a security profile for the asset hosting that service, restricting access to it only from your internal hosts. This rule could be enabled over the weekend, when Sales are not working, and on the next working day the IT team could take further action to remediate the risk accordingly.
When the vulnerability has been resolved and EVM reevaluates the web server again, the risk score is lowered. EPP will then automatically revert to the security profile that was previously used for that asset, allowing access from the Internet, too.