2023’s ransomware rookies are a remix of Conti and other classics
Ransomware is likely the one cyber security problem everyone from CISOs to customer service agents recognize as a significant threat.
Its resilient and lucrative business model (basically extorting companies by holding their data hostage) and substantial profits have helped it earn this notoriety. And despite years of government and industry efforts to push back against the problem, it has persisted (even thrived).
Ransomware’s business model is a big part of what’s made it such a potent threat for so many years. However, Threat Intelligence Analyst Ziggy Davies dug into multi-point ransomware attacks from 2023, and found another factor in ransomware’s staying power: a seemingly endless supply of new cyber crime groups starting ransomware operations.
Ransomware’s surging…again

Comparing the first three quarters of 2023 with the same period the year before, data leaks from multi-point ransomware groups (who use ransomware/destructive techniques to hinder a target’s operations, but also steal data and further extort the organization through the threat of leaking data on the dark web) surged by nearly 50%. In fact, there’s been more advertised leaks in the first 9 months of this year than all of 2022. Ransomware operators have definitely been busy.
‘New’ groups have played an important role in this increase. They accounted for nearly half of all the multi-point extortion ransomware groups tracked by WithSecure this year. And about a quarter of all the leaks, with Akira and 8base being particularly prominent sources. They’ve also been responsible for some of the year’s most notable incidents, such as Rhysida’s attack on Prospect Medical Holdings.
New but old
While there are many new groups, they often have connections to older operations. And at least one thing that has helped drive the creation of new groups is the release of code used in malware. Code re-use is one way that researchers can track the lineage of different groups.
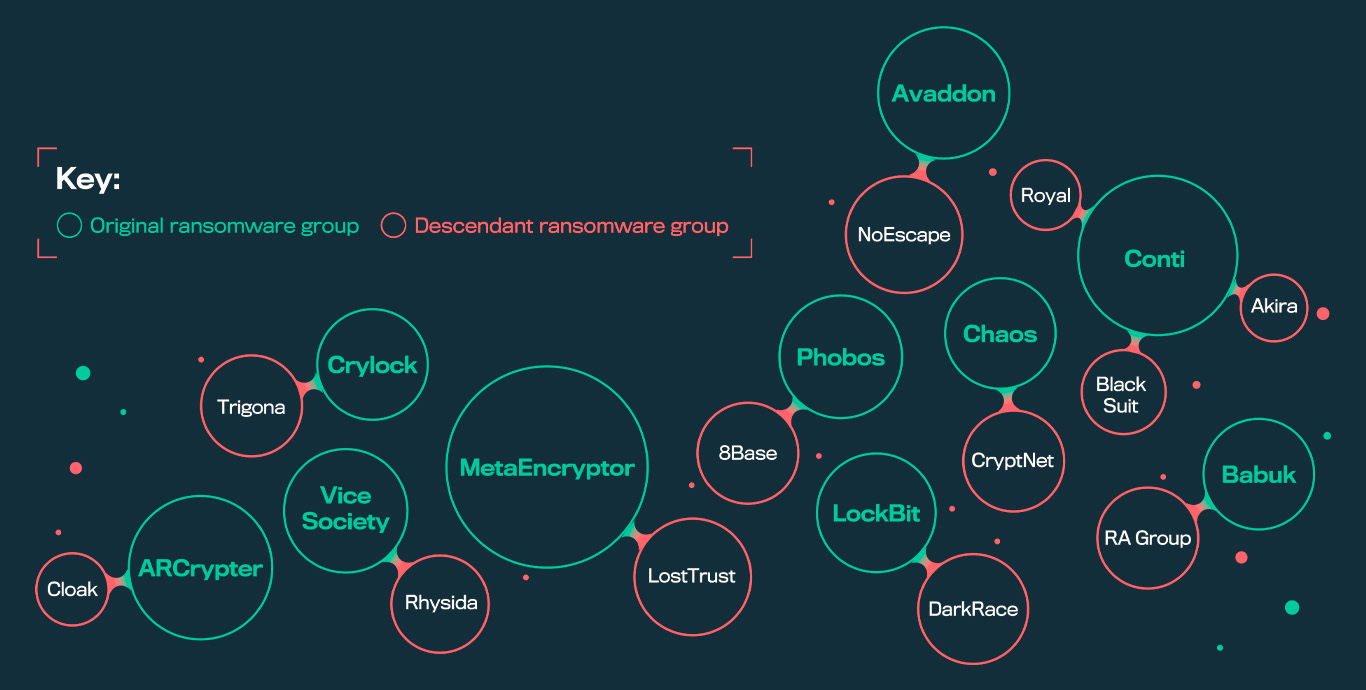
Conti, for example, was one of the most notorious operations active in recent years. According to our recent Professionalization of Cyber Crime report, they were behind numerous high-profile attacks, including the Health Service Executive of the Republic of Ireland, the Waikato District Health Board of New Zealand, the central bank of the Republic of Indonesia, The National Directorate of Intelligence of Peru, and multiple agencies of the Costa Rican government.
They somewhat dramatically dissolved in 2022 after publicly coming out in support of Russia’s invasion of Ukraine, which reportedly lead to the leak of Conti’s own data to the public. The leak included data like chat logs, training materials, tools, and source code. Conti disbanded shortly after.
However, the availability of Conti resources helped several other operations get off the ground. Royal, Akira, and Black Suit are just a few of the groups whose lineage can be traced back to Conti. And this genealogical pattern isn’t limited to Conti. The source code for Lockbit and Babuk was also leaked by disgruntled associates, and found use by other ransomware gangs.
Data leaks aren’t the only thing that leads to older groups cross-pollinating younger ones. Ransomware gangs have staff just like an IT company. And like an IT company, people change jobs sometimes, and bring their unique skills and knowledge with them. Unlike legit IT companies, however, there’s nothing stopping a cyber criminal from taking proprietary resources (such as code or tools) from one ransomware operations and using it at another. There’s no honor among thieves.
The silver lining for defenders
Old groups, however, are still very significant in multiple ways. For starters, most groups don’t last that long. Only 6 of the 60 tracked in the analysis were active every month. These groups start, stop, fold, rebrand themselves, etc. Only a few seem to have successful, sustainable operations.
And these established groups tend to be titans of their industries. Lockbit, who were responsible for attacks against Boeing, Royal Mail, and the recent attack against the Industrial and Commercial Bank of China's U.S. arm, have been the biggest source of leaks in 2023. Alphv (who were involved in the MGM Resorts International and Barts Health NHS Trust attacks) also ranked among the largest in 2023. In fact, the 5 biggest groups (Lockbit, 8Base, Alphv/BlackCat, Clop, and Play) in the accounted for over 50% of the leaked data. Lockbit, Alphv, and Clop were also the biggest players in 2022.

But what’s more important than the established gangs are the established conventions: the influence of ransomware is derived from the success yielded by its typical approach. Because of this incredible success (which is so extreme it’s essentially funding the growth of the entire cybercrime ecosystem), there’s very little need for invention.
While this success can hardly give cause for celebration, the lack of innovation is a boon for defenders. If ransomware’s evolution consists of Darwinian variations of the same basic things, organizations can pretty much know what to expect and prepare for the inevitable day when ransomware gangs knock on their digital door.